Digital Safety & Cyber Hygiene
When we look around us, we are all digitally connected through one medium or another. We all exist in at least one digital form on the Internet. When we are “online”, we leave digital trails in the form of cookies, location data, search history and email exchanges. Services that we don’t even use may have information about us. And once something is online, it stays there forever.
A breakdown of World Wide Web and how we connect to each of its segment is shown below:
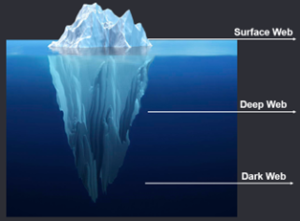
Surface Web: Any publicly searchable content falls under surface web. All our everyday activities like social networking and reading news happens here. All search engine results that pop up when you “Google” something, is part of the surface web. It comprises of roughly 4% of total internet traffic.
Deep Web: There’s nothing scary and nothing to fear about the deep web if your data is encrypted. All the data on deep web is only accessible with a set of credentials and could be data such as your medical records, educational records, online banking information, emails, and other corporate data. It accounts for over 90% of the total internet traffic.
Dark Web: This secret area of the world wide web is made up of highly encrypted network whose content is only accessible via a special browser or application such as Tor. This is the hidden corner of the internet where privacy is paramount. Due to the privacy level that it offers to users trying to stay anonymous, it also attracts criminal activity such as illegal dealings of drugs, firearms, and stolen credit cards. It is estimated to hold around 6% of total internet traffic.
Work technology and home technology are no longer two separate things. Our personal smartphones practically help us with our work-related tasks and emails every day. Sure, our organization may have relevant security policies set but adhering to them is our responsibility. Security policies being followed in any organization should be replicated at home too.
According to an article published by TerraNova Security, security awareness also cultivates a culture and mindset that prioritizes protection of sensitive information. Once this mindset becomes second nature, we can easily adapt to the ever-changing, complex world of cyber threats. Organizations often conduct cybersecurity awareness sessions for their employees to ensure corporate data is secure. This awareness must be reflected in our personal lives as well.
Technology alone doesn’t provide us with foolproof protection from cyber-attacks and data breaches. A human-centric cyber security approach is the best defense against cyber criminals. Opportunities for physical crimes declines with improvements in physical security controls such as surveillance cameras, motion sensors and biometric locks that trigger alarms. On the other hand, cybercrimes have increased with the spread of internet. These crimes are sophisticated and largely technology driven. Anyone could be a victim to cybercrimes, given the exponential rise in accessibility to the internet by almost all age groups.
Some of the most common types of cybercrimes are:
- Cyber Stalking & Cyber Bullying:
Cyberstalking is the act of persistent and unwanted contact from someone online. It usually involves threats, defamation, sexual harassment, or other actions where the perpetrator tries to control, influence, or intimidate their victims. Around 36.5% of people claim they have been cyberbullied in their lifetime, but only 17.4% have reported it. There was a 70% increase in the amount of bullying/hate speech among teens and children in the early months of the covid lockdown.
- Phishing:
Phishing is a type of attack in which the attacker sends messages pretending to be a trusted person or entity. Phishing messages are often intended to manipulate a user, causing them to perform actions like clicking a malicious link, divulging sensitive information or installing a malicious file. It is the most common type of social engineering attack. Around 3 Billion phishing emails are sent everyday which accounts to only 1% of global email traffic. Phishing often results in threats such as installation of a malware, code injection, and network attacks.
- Smishing / Vishing:
Phishing over SMS or over Voice calls is one of the most lethal social engineering attacks. Smishing targets recipients by sending them a malicious link over a compelling SMS, tricking them into clicking the link, often to disclose confidential information or install a malware onto smartphones. When Smishing and phishing don’t work, attackers resort to vishing – a verbal scam in which the caller tricks its victims into providing confidential information. The victims of this cybercrime often end up with their credit card information stolen along with other monetary fraud.
- Pirated Software:
We all have at some point tried to avoid incurring costs related to software purchases. During the pandemic alone, software piracy rate increased by 30%. The problem with pirated software is that these free versions are often laced with malwares like trojans, viruses, worms and backdoors. Book publishers lose close to $300 million in author income annually due to piracy.
Third-party app stores host 99.9% of discovered mobile malware. 98% of mobile malware target Android devices.
- Romance Scams:
The definition of this is pretty clear to anyone who has watched the Netflix documentary ‘Tinder Swindler’. Romance scams occur when a criminal adopts a fake online identity to gain a victim’s affection and trust. The scammer then uses the illusion of a romantic or close relationship to manipulate and/or steal from the victim. These scams were the 3rd most reported cybercrime to FBI of 2021.
- Distributed Denial of Service (DDoS):
DDoS is one of the most common types of attack against organizations. The attackers use bot accounts to flood the internet traffic of an organization’s services (for example, a website), thus denying others access to the service and eventually bringing down the service. These attacks may not necessarily cause a data breach but could result in reputational damage or act as a smokescreen for a ransomware attack.
- Ransomware:
The consequent result for victims of a phishing or vishing attack is often a ransomware attack. Once the attacker has your confidential data, they hold it until a ransom amount is paid. In 2021 alone, the average cost of a ransomware attack was roughly USD170,000. Anyone can fall victim to this attack, from individuals to small enterprises to large organizations.
- Cryptojacking:
Another consequence of a phishing attack where the victim may have clicked on a malicious link could result in the attacker being able to use the victim’s device’s computing power to generate cryptocurrency. Malicious programmes called ‘coin-miners’ are installed on the victim’s devices to mine cryptocurrency. Since nothing is stolen from the victim, this crime is only detected when the victim incurs high electricity and computing power bills.
Although not all cybercrimes are avoidable, we can always stay vigilant and protect ourselves and those around us with pro-active security measures. Cyber hygiene is the responsibility of every individual – within an organization and outside.
A few cyber-safety tips to follow are listed below:
1. Get your 2-FA on
Use 2-factor authentication everywhere you can. Set it up to receive authentication codes through SMS, emails or on an authenticator app.
2. Limit public Wi-Fi activity
Enable “Ask to join networks” when using public networks. Do not access sensitive data or change password on public network.
3. Be careful what you click
Avoid visiting unknown websites or downloading software from untrusted sources. Use “incognito mode” to avoid tracking and protect your privacy.
4. Restrict social media
Limit who can view your posts to friends that you actually know. Setup restrictions on your social media accounts for people to add you in groups automatically.
5. Payments through trusted channels
Make payments through trusted E-channels. Be cautious of merchants that bypass OTP’s when making online payments. Do not register for auto payments.
6. Never leave devices unattended
If you need to leave your laptop, phone, or tablet for any length of time, lock it so no one else can use it.
7. Safe online shopping
Never shop online from a device that isn’t yours or on a network you don’t own. Don’t let “act now” deals pressure you into a payment.
8. Security Patches
Make sure to deploy latest security patches on your personal computers and smart devices on a frequent basis.
Arshiyan Bhure
Batelco – Network Security Specialist
References:
https://terranovasecurity.com/security-awareness-training/
https://security.ucop.edu/resources/security-awareness/privacy-2019.html
https://www.fbi.gov/how-we-can-help-you/safety-resources/scams-and-safety/
